How to set up Remote Desktop Connection
Windows Azure allows you to Remote Desktop to any of your deployment instances. Follow this how to for the setup.
We need a tool called CSEncrypt Command-Line Tool, you can get it by installing Windows Azure SDK for .NET. Download WindowsAzureLibsForNet-x64.msi or x86.msi then you should be able to find it at the default installation path: C:\Program Files\Microsoft SDKs\Windows Azure\.NET SDK\2012-10\bin
Run a Command window and type
CSEncrypt Get-PasswordEncryptionCertificate
The output is something like this, a list of all the certificates that are usable for encryption on your machine.
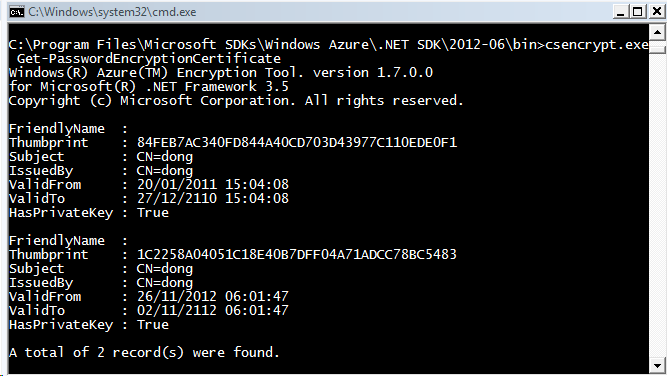
To create a new one, we type
CSEncrypt New-PasswordEncryptionCertificate -FriendlyName MyFourtyTwoRDPCert
This one has longer output but if you run the first command again, you should see the newly created one listed there.
Now let's encrypt the RDP password:
CSEncrypt Encrypt-Password -Output t:\dong\FourtyTwoRDPPass.txt -Thumbprint DF9913DA63103F0D62C7FC02E5B5A52732E65FA3
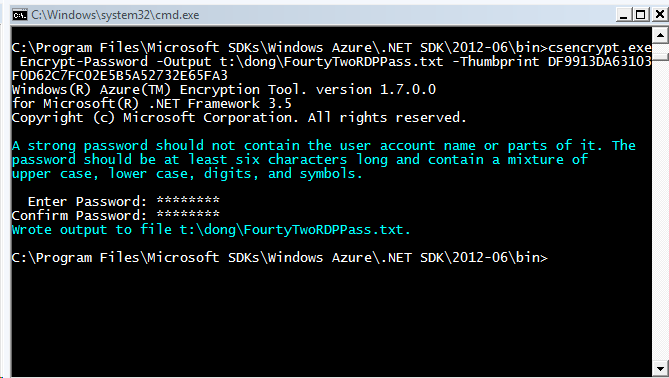
Note you might not able to write to the SDK path so use a writable path like C:\Users\somebody; the Thumbprint is what we got from the step before. If success, in the text file we have a long string which is an encrypted password you just typed.
We are done with CSEncrypt, let's switch to PowerShell to get the certificate file itself, you need to upload this file to Windows Azure Portal.
ls cert:\CurrentUser\My
This will list certificates including our newly created one, you can check on the Thumbprint value, then starting from 0, count the position of this cert, e.g. 2, you shall be able to see the same cert if you do
(ls cert:\CurrentUser\My)[2]
Now type those code:
$bytes = (ls cert:\CurrentUser\My)[2].export([System.Security.Cryptography.X509Certificates.X509ContentType]::pfx, "StrongPassword")
[System.IO.File]::WriteAllBytes("t:\dong\FourtytwoRDPCert.pfx", $bytes)
Note this 'StrongPassword' is not the same as our RDP password, this one is used to encrypt the pfx file, so please use a real strong one and keep it somewhere secure. This .pfx file is what we need. You can double check if everything is alright by
Get-PfxCertificate t:\dong\FourtytwoRDPCert.pfx
It will ask for the password and show the output with Thumbprint you can verify. (BTW if you are using Windows Server 2012, there is a new PowerShell comlet you can use for this purpose in one go: Export-PfxCertificate
Summary
After this How to you shall have the following things ready:
- a text file holding the encrypted password in a long string
- a pfx file holding the cert and private key in one file
- the password you used to encrypt the pfx file
- the password you typed that's going to be used for RDP login
- the Thumbprint for this cert